 ] Type Year
] Type Year IEEE Security & Privacy , vol. 20, issue 1, IEEE, pp. 23 - 32, 01/2022. DOI
Abstract
This article introduces a privacy manager for IoT data based on Edge Computing. This poses the advantage that privacy is enforced before data leaves the control of the user, who is provided with a tool to express data sharing preferences based on a novel context-aware privacy language.

International Conference on Information Systems Education and Research (AIS SIGED 2019), 12/2019.

Information Security Practice and Experience (ISPEC 2014), vol. 8434, Springer, pp. 15-27, 05/2014. DOI
Abstract
Wireless sensor networks (WSNs) are exposed to many different types of attacks. Among these, the most devastating attack is to compromise or destroy the base station since all communications are addressed exclusively to it. Moreover, this feature can be exploited by a passive adversary to determine the location of this critical device. This receiver-location privacy problem can be reduced by hindering traffic analysis but the adversary may still obtain location information by capturing a subset of sensor nodes in the field. This paper addresses, for the first time, these two problems together in a single solution

VII Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2022), pp. 122-129, 06/2022.
Abstract
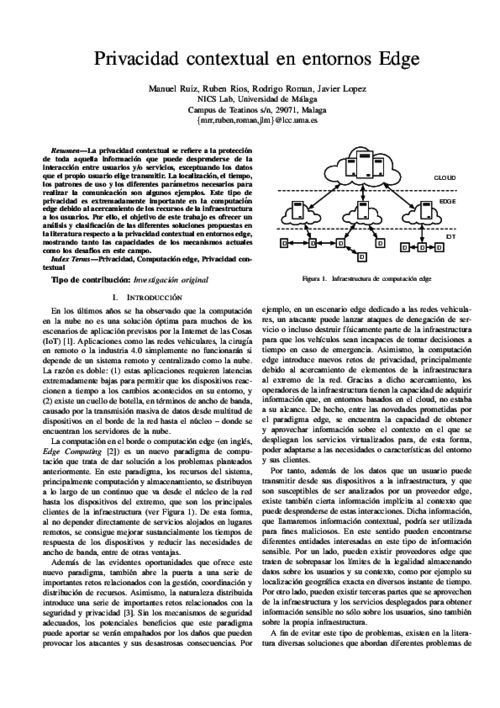
La privacidad contextual se refiere a la protección de toda aquella información que puede desprenderse de la interacción entre usuarios y/o servicios, exceptuando los datos que el propio usuario elige transmitir. La localización, el tiempo, los patrones de uso y los diferentes parámetros necesarios para realizar la comunicación son algunos ejemplos. Este tipo de privacidad es extremadamente importante en la computación edge debido al acercamiento de los recursos de la infraestructura a los usuarios. Por ello, el objetivo de este trabajo es ofrecer un análisis y clasificación de las diferentes soluciones propuestas en la literatura respecto a la privacidad contextual en entornos edge, mostrando tanto las capacidades de los mecanismos actuales como los desafíos en este campo.
Computers & Security, vol. 39 (B), Elsevier, pp. 117-126, 11/2013. DOI
Abstract
Continuous authentication is mainly associated with the use of biometrics to guarantee that a resource is being accessed by the same user throughout the usage period. Wireless devices can also serve as a supporting technology for continuous authentication or even as a complete alternative to biometrics when accessing proximity-based services. In this paper we present the implementation of a secure, non-invasive continuous authentication scheme supported by the use of Wearable Wireless Devices (WWD), which allow users to gain access to proximity-based services while preserving their privacy. Additionally we devise an improved scheme that circumvents some of the limitations of our implementation.

Security and Privacy for Big Data, Cloud Computing and Applications, Lizhe Wang, Wei Ren, Raymoond Choo and Fatos Xhafa, The Institution of Engineering and Technology (IET) , 09/2019.

12th International Workshop on Security and Trust Management (STM), vol. LNCS 9871, Springer, pp. 98-105, 09/2016. DOI
Abstract
Software engineering and information security have traditionally followed divergent paths but lately some efforts have been made to consider security from the early phases of the Software Development Life Cycle (SDLC). This paper follows this line and concentrates on the incorporation of trust negotiations during the requirements engineering phase. More precisely, we provide an extension to the SI* modelling language, which is further formalised using answer set programming specifications to support the automatic verification of the model and the detection of privacy conflicts caused by trust negotiations.

Information Sciences, vol. 321, Elsevier, pp. 205 - 223, 07/2015. DOI
Abstract
Wireless sensor networks (WSNs) are continually exposed to many types of attacks. Among these, the attacks targeted at the base station are the most devastating ones since this essential device processes and analyses all traffic generated in the network. Moreover, this feature can be exploited by a passive adversary to determine its location based on traffic analysis. This receiver-location privacy problem can be reduced by altering the traffic pattern of the network but the adversary may still be able to reach the base station if he gains access to the routing tables of a number of sensor nodes. In this paper we present HISP-NC (Homogenous Injection for Sink Privacy with Node Compromise protection), a receiver-location privacy solution that consists of two complementary schemes which protect the location of the base station in the presence of traffic analysis and node compromise attacks. The HISP-NC data transmission protocol prevents traffic analysis by probabilistically hiding the flow of real traffic with moderate amounts of fake traffic. Moreover, HISP-NC includes a perturbation mechanism that modifies the routing tables of the nodes to introduce some level of uncertainty in attackers capable of retrieving the routing information from the nodes. Our scheme is validated both analytically and experimentally through extensive simulations.

XIII Jornadas de Ingeniería Telemática (JITEL 2017), vol. Libro de actas, Editorial Universitat Politècnica de València, pp. 302-309, 01/2018, 2017. DOI
