IEEE Transactions on Information Forensics & Security, vol. 15, IEEE, pp. 3325-3334, 17/04/2020. DOI
Abstract
One of the biggest challenges in IoT-forensics is the analysis and correlation of heterogeneous digital evidence, to enable an effective understanding of complex scenarios. This paper defines a methodology for extracting unique objects (e.g., representing users or devices) from the files of a case, defining the context of the digital investigation and increasing the knowledge progressively, using additional files from the case (e.g. network captures). The solution includes external searches using open source intelligence (OSINT) sources when needed. In order to illustrate this approach, the proposed methodology is implemented in the JSON Users and Devices analysis (JUDAS) tool, which is able to generate the context from JSON files, complete it, and show the whole context using dynamic graphs. The approach is validated using the files in an IoT-Forensic digital investigation where an important set of potential digital evidence extracted from Amazon’s Alexa Cloud is analysed.

Human-centric Computing and Information Sciences, vol. 9, no. 1, Springer, pp. 1-23, 2019. DOI
International Conference on Information Systems Education and Research (AIS SIGED 2019), 12/2019.

Security and Privacy for Big Data, Cloud Computing and Applications, Lizhe Wang, Wei Ren, Raymoond Choo and Fatos Xhafa, The Institution of Engineering and Technology (IET) , 09/2019.

The 16th IEEE International Conference on Dependable, Autonomic and Secure Computing (DASC 2018), pp. 536-543, 08/2018. DOI
Abstract
In the current telecommunications landscape, different devices, systems and platforms are constantly communicating with each other. This heterogeneous environment creates the perfect situation for attacks to pass from one platform to another. This is a particularly worrying scenario, because of the new technologies being used (such as network slicing in 5G), the increasing importance of connected devices in our lives (IoT), and the unpredictable consequences that an attack of this type could have. The current approaches in attack analysis do not take into account these sitations, and the attacker/victim paradigm usually followed may fall short when dealing with these attacks. Thus, in this paper, an architecture for the analysis of cross-platform attacks will be presented, aiming to help understand better this kind of threats and offering solutions to mitigate and track them.

The 16th IEEE International Conference on Dependable, Autonomic and Secure Computing (DASC 2018), IEEE, pp. 520-527, 08/2018. DOI
Abstract
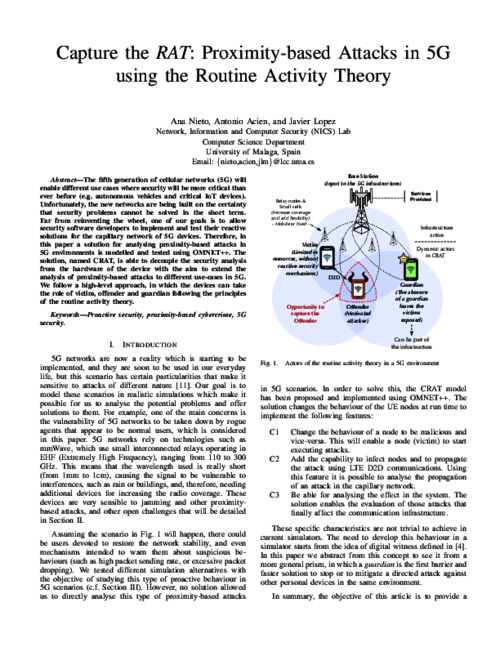
The fifth generation of cellular networks (5G) will enable different use cases where security will be more critical than ever before (e.g. autonomous vehicles and critical IoT devices). Unfortunately, the new networks are being built on the certainty that security problems can not be solved in the short term. Far from reinventing the wheel, one of our goals is to allow security software developers to implement and test their reactive solutions for the capillary network of 5G devices. Therefore, in this paper a solution for analysing proximity-based attacks in 5G environments is modelled and tested using OMNET++. The solution, named CRAT, is able to decouple the security analysis from the hardware of the device with the aim to extend the analysis of proximity-based attacks to different use-cases in 5G. We follow a high-level approach, in which the devices can take the role of victim, offender and guardian following the principles of the routine activity theory.
15th International Conference on Trust, Privacy and Security in Digital Business (TrustBus 2018), vol. LNCS 11033, Springer Nature Switzerland AG, pp. 229–243, 09/2018. DOI
Abstract
Recent news have raised concern regarding the security on the IoT field. Vulnerabilities in devices are arising and honeypots are an excellent way to cope with this problem. In this work, current solutions for honeypots in the IoT context, and other solutions adaptable to it are analyzed in order to set the basis for a methodology that allows deployment of IoT honeypot.

Mobile Networks and Applications (MONET), Springer US, pp. 881-889, 10/2018. DOI
Abstract
Crowdsourcing can be a powerful weapon against cyberattacks in 5G networks. In this paper we analyse this idea in detail, starting from the use cases in crowdsourcing focused on security, and highlighting those areas of a 5G ecosystem where crowdsourcing could be used to mitigate local and remote attacks, as well as to discourage criminal activities and cybercriminal behaviour. We pay particular attention to the capillary network, where an infinite number of IoT objects coexist. The analysis is made considering the different participants in a 5G IoT ecosystem.

XV Reunión Española sobre Criptología y Seguridad de la Información, 10/2018.
Abstract
Con la revolución tecnológica que ha supuesto la Internet de las Cosas (Internet of Things, IoT) se han presentado escenarios donde la preocupación por la seguridad en dicho entorno es cada vez más relevante. Están comenzando a surgir vulnerabilidades en varios dispositivos, y los sistemas trampa son una excelente manera de lidiar con este problema. En este trabajo se analizan soluciones para honeypots en el entorno IoT (y en otros que se puedan adaptar) para sentar las bases de una metodología que permita el despliegue de honeypots IoT.

Sensors, vol. 18, issue 2, no. 492, MDPI, 02/2018. DOI
Abstract
IoT-Forensics is a novel paradigm for the acquisition of electronic evidence whose operation is conditioned by the peculiarities of the Internet of Things (IoT) context. As a branch of computer forensics, this discipline respects the most basic forensic principles of preservation, traceability, documentation, and authorization. The digital witness approach also promotes such principles in the context of the IoT while allowing personal devices to cooperate in digital investigations by voluntarily providing electronic evidence to the authorities. However, this solution is highly dependent on the willingness of citizens to collaborate and they may be reluctant to do so if the sensitive information within their personal devices is not sufficiently protected when shared with the investigators. In this paper, we provide the digital witness approach with a methodology that enables citizens to share their data with some privacy guarantees. We apply the PRoFIT methodology, originally defined for IoT-Forensics environments, to the digital witness approach in order to unleash its full potential. Finally, we show the feasibility of a PRoFIT-compliant digital witness with two use cases.

IV Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2018), Servicio Editorial de Mondragon Unibertsitatea, 06/2018.
Abstract
Los ataques cross-platform suponen un serio desafío para los mecanismos de seguridad cuando los portadores de un ataque dirigido no son conscientes de su participacion en el mismo. Es por ello que, con dispositivos y tecnologías cada vez mas entrelazadas, en constante comunicación, numerosos ataques pasan desapercibidos hasta que alcanzan su objetivo final. Estos nuevos escenarios hacen posible una vía de transmision a tener en cuenta, y que se debe abordar cuanto antes, ya que sus consecuencias, especialmente en el panorama de telecomunicaciones actual, podrían ser desoladoras. La rapida transmisión de estos ataques, y la dificultad que supone su prevencion, detección y mitigación antes de que se hagan efectivos, hacen que el problema sea particularmente preocupante. En este artículo se presentará una arquitectura para el analisis de los ataques cross-platform silenciosos, cuyo objetivo es ayudar a comprender mejor este tipo de amenazas y ofrecer soluciones que permitan mitigarlas y rastrearlas.

IEEE 5G World Forum (5GWF), IEEE, pp. 191-196, 07/2018. DOI
Abstract
This article analyses the state of the art of proactive forensic solutions and highlights the importance of preparing the 5G ecosystem to serve digital forensic purposes. The analysis considers the current 5G threat landscape from the ENISA report, and discusses how some of the attacks could be mitigated using proactive forensic mechanisms. In addition, the requirements for deploying proactive forensic solutions in 5G are classified, and analysed based on the specific threats against 5G.

III Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2017), Servicio de Publicaciones de la URJC, pp. 91-98, 06/2017.
Abstract
Este trabajo propone una arquitectura de despliegue de honeypots adaptativos, configurados dinámicamente a partir de los requisitos del malware que intenta infectar los servicios trampa. A diferencia de otros trabajos sobre honeypots adaptativos, los mecanismos de adaptabilidad aquí diseñados tomarán como base información de inteligencia sobre amenazas actuales, indicadores de compromiso (IOCs) conocidos, así como información de actividades sospechosas actualmente en estudio por los analistas. Este conocimiento será empleado para configurar honeypots de manera dinámica, permitiendo satisfacer los requisitos necesarios para que el malware pueda desplegar toda su operativa.

16th IEEE International Conference On Trust, Security And Privacy In Computing And Communications (TrustCom 2017), IEEE, pp. 642-649, 08/2017. DOI
Abstract
The digital witness approach defines the collaboration between IoT devices - from wearables to vehicles - to provide digital evidence through a Digital Chain of Custody to an authorised entity. As one of the cores of the digital witness, binding credentials unequivocally identify the user behind the digital witness. The objective of this article is to perform a critical analysis of the digital witness approach from the perspective of privacy, and to propose solutions that help include some notions of privacy in the scheme (for those cases where it is possible). In addition, digital anonymous witnessing as a tradeoff mechanism between the original approach and privacy requirements is proposed. This is a clear challenge in this context given the restriction that the identities of the links in the digital chain of custody should be known.

IEEE Systems Journal, vol. 11, issue 4, no. 99, IEEE, pp. 2479-2489, 12/2017. DOI
Abstract
The growing number of parameters in heteroge- neous networks, as is the case of the fifth generation (5G) Green networks, greatly complicates the analysis of the Security and Quality of Service Tradeoff (SQT). However, studying these types of relationships is crucial in Future Internet scenarios to prevent potential points of failure and to enhance the use of limited resources, increasing the user’s experience. Therefore, it is fundamental to provide tools and models for training, so that the users understand these dependencies and solve them prior to deploying new solutions. In this paper, a Recommendation System for SQT (SQT-RS) is deployed in 5G Green systems, considering the particular case of relay networks and the impact of eavesdropping and jamming contexts on the models generated by the user, aided by SQT-RS. With this goal in mind, we provide a component for the user to automatically select specific contexts based on 5G Green capabilities.

16th IEEE International Conference On Trust, Security And Privacy In Computing And Communications (TrustCom 2017), IEEE, pp. 626-633, 08/2017. DOI
Abstract
The Internet of Things (IoT) brings new challenges to digital forensics. Given the number and heterogeneity of devices in such scenarios, it bring extremely difficult to carry out investigations without the cooperation of individuals. Even if they are not directly involved in the offense, their devices can yield digital evidence that might provide useful clarification in an investigation. However, when providing such evidence they may leak sensitive personal information. This paper proposes PRoFIT; a new model for IoT-forensics that takes privacy into consideration by incorporating the requirements of ISO/IEC 29100:2011 throughout the investigation life cycle. PRoFIT is intended to lay the groundwork for the voluntary cooperation of individuals in cyber crime investigations.

14th International Conference On Trust, Privacy & Security In Digital Business (TrustBus 2017), vol. 10442, Springer International Publishing, pp. 130-144, 08/2017. DOI
Abstract
In this paper we propose the Hogney architecture for the deployment of malware-driven honeypots. This new concept refers to honeypots that have been dynamically configured according to the environment expected by malware. The adaptation mechanism designed here is built on services that offer up-to-date and relevant intelligence information on current threats. Thus, the Hogney architecture takes advantage of recent Indicators Of Compromise (IOC) and information about suspicious activity currently being studied by analysts. The information gathered from these services is then used to adapt honeypots to fulfill malware requirements, inviting them to unleash their full strength.

XIII Jornadas de Ingeniería Telemática (JITEL 2017), vol. Libro de actas, Editorial Universitat Politècnica de València, pp. 302-309, 01/2018, 2017. DOI

III Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2017), vol. Actas del JNIC 2017, Servicio de Publicaciones de la URJC, pp. 51-58, 2017.

XIV Reunión Española sobre Criptología y Seguridad de la Información, pp. 168-173, 10/2016.
Abstract
En la Internet de los Objetos (IoT, por sus siglas en inglés), los ataques pueden ser perpetrados desde dispositivos que enmascaran su rastro ayudándose de la densidad de objetos y usuarios. Actualmente la idea de que los dispositivos de usuario almacenan evidencias que pueden ser muy valiosas para frenar ataques es bien conocida. Sin embargo, la colaboración de éstos para denunciar posibles abusos telemáticos aún está por definir. Los testigos digitales son dispositivos concebidos para definir la participación de dispositivos de usuario en una cadena de custodia digital. La idea es que las evidencias se generan, almacenan y transfieren siguiendo los requisitos marcados por las normas actuales (p.ej. UNE 71505), pero respetando las restricciones en recursos de los dispositivos. En este artículo proponemos una arquitectura funcional para la implementación del concepto de testigo digital en dispositivos heterogéneos de la IoT.

ERCIM News, no. 106, ERCIM EEIG, pp. 9-9, 07/2016.
IEEE Network, IEEE Communications Society, pp. 12-19, 2016. DOI
Abstract
Personal devices contain electronic evidence associated with the behaviour of their owners and other devices in their environment, which can help clarify the facts of a cyber-crime scene. These devices are usually analysed as containers of proof. However, it is possible to harness the boom of personal devices to define the concept of digital witnesses, where personal devices are able to actively acquire, store, and transmit digital evidence to an authorised entity, reliably and securely. This article introduces this novel concept, providing a preliminary analysis on the management of digital evidence and the technologies that can be used to implement it with security guarantees in IoT environments. Moreover, the basic building blocks of a digital witness are defined.

Revista SIC, vol. 122, Ediciones CODA, pp. 94-98, Nov 2016.
Abstract
El creciente número de dispositivos interconectados trae consigo problemas de seguridad bien conocidos; por ejemplo, aquellos debidos a las vulnerabilidades en protocolos muy diversos –muchos de ellos propietarios– y al factor de error humano introducido por los usuarios. Sin embargo, cabe preguntarse cómo podemos usar el despliegue de tales dispositivos en beneficio de la ciberseguridad. En el proyecto IoTest se está desarrollando una solución, el Testigo Digital, que permitirá a los dispositivos personales con arquitectura de seguridad embebida reaccionar ante ataques virtuales, protegiéndonos de los ciberataques emergentes.

II Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2016), pp. 109-116, 06/2016.
Abstract
En un mundo en el que los usuarios dependen cada vez más de sus dispositivos, éstos almacenan gran cantidad de datos y son una fuente muy valiosa de información sobre su entorno. Sin embargo, la heterogeneidad y la densidad de los objetos conectados, características propias de la Internet de las Cosas (IoT), sirven de velo para ocultar conductas maliciosas que afectan a estos dispositivos, sin que quede rastro de tales acciones. En este artículo definimos el concepto de testigo digital: funcionalidad que permitirá a los dispositivos personales y otros objetos colaborar para implementar una cadena de custodia digital en la IoT. El fin perseguido es ofrecer soluciones que mitiguen los efectos de la ciberdelincuencia, amparándose en la colaboración de los dispositivos con arquitecturas de seguridad embebidas para alertar de conductas maliciosas, y dejar constancia de éstas.

Computer Communications, vol. 68, Elsevier, pp. 33-46, 09/2015. DOI
Abstract
The lack of abstraction in a growing semantic, virtual and abstract world poses new challenges for assessing security and QoS tradeoffs. For example, in Future Internet scenarios, where Unified Communications (UC) will take place, being able to predict the final devices that will form the network is not always possible. Without this information the analysis of the security and QoS tradeoff can only be based on partial information to be completed when more information about the environment is available. In this paper, we extend the description of context-based parametric relationship model, providing a tool for assessing the security and QoS tradeoff (SQT) based on interchangeable contexts. Our approach is able to use the heterogeneous information produced by scenarios where UC is present.

Telecommunication Systems , vol. 59, issue 1, Springer US, pp. 169-187, 05/2015. DOI
Abstract
In this article, we present relay selection policies in applications with secrecy requirements which are of interest in the fifth generation (5G) of wireless networks. More specifically, we provide a classification of relays based on their distinct communication attributes, such as processing, multiple antennas, storage, channel estimation, density and security level. In addition, we discuss the level of efficiency exhibited by each relay class, regarding their impact in delay-critical applications and green communications applications, while aiming at a specific security level at the physical layer. Then, relay selection policies are proposed taking into consideration the goals set by each application. Numerical evaluation of the proposed policies in terms of the average secrecy rate, average delay and power reduction show improved performance compared to other state-of-the-art solutions.
España, C. Autón./Reg. de explotación: Andalucía, Invention Patent, vol. P201500764, G06F 21/00, 10/2015.
IEEE International Conference on Communications (ICC'14), IEEE Communications Society, pp. 755-760, 06/2014. DOI
Abstract
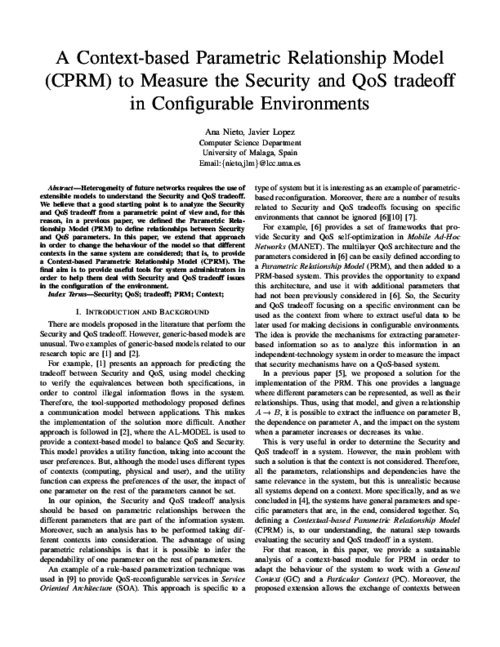
Heterogeneity of future networks requires the use of extensible models to understand the Security and QoS tradeoff. We believe that a good starting point is to analyze the Security and QoS tradeoff from a parametric point of view and, for this reason, in a previous paper, we defined the Parametric Rela- tionship Model (PRM) to define relationships between Security and QoS parameters. In this paper, we extend that approach in order to change the behaviour of the model so that different contexts in the same system are considered; that is, to provide a Context-based Parametric Relationship Model (CPRM). The final aim is to provide useful tools for system administrators in order to help them deal with Security and QoS tradeoff issues in the configuration of the environment.
9th International Conference on Risk and Security of Internet and Systems (CRiSIS'14), vol. 8924, Springer, pp. 52-66, 2014. DOI
Abstract
Context-based Parametric Relationship Models (CPRMs) reduce the complexity of working with various numbers of parameters and dependencies, by adding particular contexts to the final scheme when it is required, dynamically. In this paper the cost of including new information in CPRM is properly analysed, considering the information in the parametric trees defined for the parameters in the CPRM-based system. Some strategies for mitigating the cost of the instantiation process are proposed.

XIII Reunión Española sobre Criptología y Seguridad de la Información (RECSI 2014), pp. 303-308, 09/2014.
Abstract
El análisis conjunto de mecanismos de seguridad y QoS es esencial para las redes heterogéneas donde diversos dispositivos pueden coexistir en entornos dinámicos. En concreto, los dispositivos no siempre pueden ser conocidos, por lo que diferentes requisitos y mecanismos pueden surgir para el análisis. En este artículo, proponemos una herramienta para facilitar la configuración de entornos basada en el análisis paramétrico de dependencias, tomando como base de conocimiento un conjunto de parámetros de seguridad y QoS. Esta forma de análisis de parámetros a alto nivel permite considerar las dependencias y la compensación entre mecanismos con independencia del sistema de información subyacente. Posibilita por tanto evaluar el impacto que tales mecanismos, y otros definidos acorde al modelo, tienen sobre un sistema previo a su despliegue.

Mobile Networks and Applications (MONET) Journal, vol. 19, issue 1, Springer US, pp. 64-78, 02/2014. DOI
Abstract
Today, mobile platforms are multimedia devices that provide different types of traffic with the consequent particular performance demands and, besides, security concerns (e.g. privacy). However, Security and QoS requirements quite often conflict to a large degree; the mobility and heterogeneous paradigm of the Future Internet makes coexistence even more difficult, posing new challenges to overcome. Probably, one of the main challenges is to identify the specific reasons why Security and QoS mechanisms are so related to each other. In this paper, we present a Parametric Relationship Model (PRM) to identify the Security and QoS dependencies, and to elaborate on the Security and QoS tradeoff. In particular, we perform an analysis that focus on the mobile platform environment and, consequently, also considers subjective parameters such user’s experience, that is crucial for increasing the usability of new solutions in the Future Internet. The final aim of our contribution is to facilitate the development of secure and efficient services for mobile platforms.

10th ACM International Symposium on QoS and Security for Wireless and Mobile Networks (Q2SWinet'14), ACM, pp. 25-32, 09/2014. DOI
Abstract
Context-based Parametric Relationship Models (CPRM) define complex dependencies between different types of parameters. In particular, Security and QoS relationships, that may occur at different levels of abstraction, are easily identified using CPRM. However, the growing number of parameters and relationships, typically due to the heterogeneous scenarios of future networks, increase the complexity of the final diagrams used in the analysis, and makes the current solution for assessing Security and QoS tradeoff (SQT) impractical for untrained users. In this paper, we define a recommendation system based on contextual parametric relationships in accordance with the definition of CPRM. The inputs for the system are generated dynamically based on the context provided by CPRM-based systems.

Security and Communication Networks (SCN) Journal, vol. 7, issue 12, Wiley-Blackwell, pp. 2778-2803, 2013. DOI
Abstract
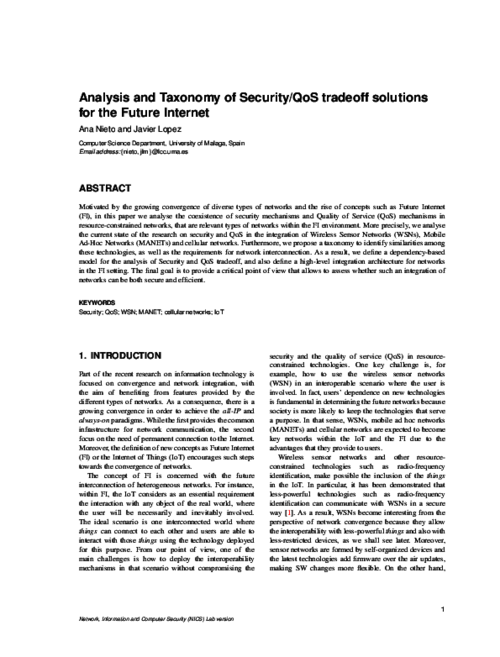
Motivated by the growing convergence of diverse types of networks and the rise of concepts such as Future Internet (FI), in this paper we analyse the coexistence of security mechanisms and Quality of Service (QoS) mechanisms in resourceconstrained networks, that are relevant types of networks within the FI environment. More precisely, we analyse the current state of the research on security and QoS in the integration of Wireless Sensor Networks (WSNs), Mobile Ad-Hoc Networks (MANETs) and cellular networks. Furthermore, we propose a taxonomy to identify similarities among these technologies, as well as the requirements for network interconnection. As a result, we define a dependency-based model for the analysis of Security and QoS tradeoff, and also define a high-level integration architecture for networks in the FI setting. The final goal is to provide a critical point of view that allows to assess whether such an integration of networks can be both secure and efficient.
The 4th FTRA International Conference on Computer Science and its Applications (CSA 2012), Lecture Notes in Electrical Engineering 203, Springer Netherlands, pp. 13-21, 2012. DOI
Abstract
Mobile platforms are becoming a fundamental part of the user’s daily life. The human-device relationship converts the devices in a repository of personal data that may be stolen or modified by malicious users. Moreover, wireless capabilities open the door to several malicious devices, and mobility represents an added difficulty in the detection of malicious behavior and in the prevention of the same. Furthermore, smartphones are subject to quality of service (QoS) restrictions, due to the user needs for multimedia applications and, in general, the need to be always-on. However, Security and QoS requirements are largely confronted and the mobility and heterogeneous paradigm on the Future Internet makes its coexistence even more difficult, posing new challenges to overcome. We analyze the principal challenges related with Security and QoS tradeoffs in mobile platforms. As a result of our analysis we provide parametric relationships between security and QoS parameters focused on mobile platforms.

Advanced Information Networking and Applications Workshops (WAINA), 2012 26th International Conference on, IEEE, pp. 745-750, 03/2012. DOI
Abstract
Motivated by the growing convergence of diverse types of networks and the raise of new concepts such as Future Internet (FI), in this paper we present an analysis of current research on the development of security mechanisms in a tradeoff with Quality of Service (QoS) mechanisms. More precisely, we pay attention to the Security and QoS problems in resource-constrained networks that are candidates to be an important part of the FI due to their proximity to the user or because of their contribution to the information society. We analyse the current state of the research on security and QoS in the integration of sensors, MANET and cellular networks, with the aim of providing a critical point of view, allowing us to assess whether it is possible that such integration of networks is both secure and efficient.

XII Reunión Española sobre Criptología y Seguridad de la Información (RECSI 2012), pp. 45-50, Sep 2012.
Abstract
En este trabajo proponemos una plataforma para el desarrollo de un sistema colaborativo para la detección y reacción ante intrusiones, empleando como base las tecnologías presentes en Intel vPro. La solución presentada está dirigida a solventar la necesidad de implantación de nuevas tecnologías que posibiliten la reacción ante ataques, independientemente del sistema operativo usado. Con este fin, en este trabajo abordamos tres puntos fundamentales: la detección de intrusiones colaborativa, la respuesta automática de los nodos ante la detección de una intrusión y el uso de herramientas que posibiliten asegurar la confianza en un nodo. En un sistema colaborativo como el que se propone aquí, un aspecto clave para la seguridad es la protección de las comunicaciones entre los mecanismos de detección y reacción frente a intrusiones. La modificación o el simple acceso a los datos intercambiados por tales sistemas supone un grave riesgo para la seguridad del entorno. Como resultado hemos desarrollado un prototipo preliminar para probar la solución propuesta en un escenario de ataque real.

Advanced Information Networking and Applications Workshops (WAINA), 2012 26th International Conference on, IEEE, pp. 607-612, 03/2012. DOI
Abstract
Wireless Sensor Networks (WSN) are networks composed of autonomous devices manufactured to solve a specific problem, with limited computational capabilities and resource-constrained (e.g. limited battery). WSN are used to monitor physical or environmental conditions within an area (e.g. temperature, humidity). The popularity of the WSN is growing, precisely due to the wide range of sensors available. As a result, these networks are being deployed as part of several infrastructures. However, sensors are designed to collaborate only with sensors of the same type. In this sense, taking advantage of the heterogeneity of WSN in order to provide common services, like it is the case of routing, has not been sufficiently considered. For this reason, in this paper we propose a routing protocol based on traffic classification and role-assignment to enable heterogeneous WSN for cooperation. Our approach considers both QoS requirements and lifetime maximization to allow the coexistence of different applications in the heterogeneous network infrastructure.

Digital Home Networking, R. Carbou, E. Exposito, and R. Roman Eds., Wiley-ISTE, pp. 17 - 58, 2011.
 ]
] 