| Title | Capture the RAT: Proximity-based Attacks in 5G using the Routine Activity Theory |
| Publication Type | Conference Paper |
| Year of Publication | 2018 |
| Authors | A. Nieto, A. Acien, and J. Lopez |
| Conference Name | The 16th IEEE International Conference on Dependable, Autonomic and Secure Computing (DASC 2018) |
| Pagination | 520-527 |
| Date Published | 08/2018 |
| Publisher | IEEE |
| Conference Location | Athens, Greece |
| ISBN Number | 978-1-5386-7518-2 |
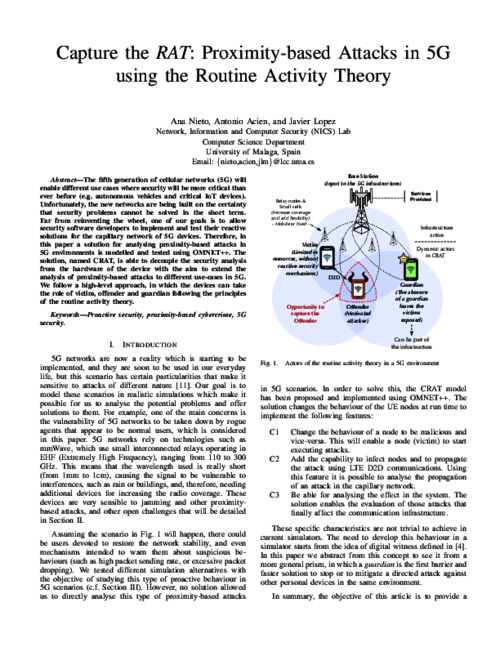
| Abstract | The fifth generation of cellular networks (5G) will enable different use cases where security will be more critical than ever before (e.g. autonomous vehicles and critical IoT devices). Unfortunately, the new networks are being built on the certainty that security problems can not be solved in the short term. Far from reinventing the wheel, one of our goals is to allow security software developers to implement and test their reactive solutions for the capillary network of 5G devices. Therefore, in this paper a solution for analysing proximity-based attacks in 5G environments is modelled and tested using OMNET++. The solution, named CRAT, is able to decouple the security analysis from the hardware of the device with the aim to extend the analysis of proximity-based attacks to different use-cases in 5G. We follow a high-level approach, in which the devices can take the role of victim, offender and guardian following the principles of the routine activity theory. |
| URL | https://ieeexplore.ieee.org/document/8511943 |
| DOI | 10.1109/DASC/PiCom/DataCom/CyberSciTec.2018.00100 |
| Citation Key | CRAT2018 |
Capture the RAT: Proximity-based Attacks in 5G using the Routine Activity Theory
Paper File:
https://nics.uma.es:8082/sites/default/files/papers/CRAT2018.pdf