]
] V Jornadas de Ingeniería Telemática (JITEL’05), pp. 375-382, September, 2005.
Abstract
Spam is considered to be one of the biggest problems in messaging systems. In the area of email Spam, A high number of anti-spam schemes have been proposed and deployed, but the problem has yet been well addressed. In this paper, we introduce a new scheme, called pre-challenge scheme, which avoids problems that exists in other schemes such as delay of service and denial of service. Some new mechanisms are employed to reach a good balance between security against Spam and convenience to email users. In addition, our scheme can be used for protecting other types of messaging systems, such as Instant Messaging (IM) and Blogs, against Spam.

20th IFIP International Information Security Conference (IFIP-SEC’05), R. Sasaki, S. Qing, E. Okamoto, and H. Yoshiura Eds., Springer, pp. 281-294, May, 2005.
Abstract
Spam turns out to be an increasingly serious problem to email users. A number of anti-spam schemes have been proposed and deployed, but the problem has yet been well addressed. One of those schemes is challenge-response, in which a challenge is imposed on an email sender. However, such a scheme introduces new problems for the users, e.g., delay of service and denial of service attacks. In this paper, we introduce a pre-challenge scheme that avoids those problems. It assumes each user has a challenge that is defined by the user himself/herself and associated with his/her email address, in such a way that an email sender can simultaneously retrieve a new receiver’s email address and challenge before sending an email in the first contact. Some new mechanisms are employed to reach a good balance between security against spam and convenience to email users.

On Foundations of Security Analysis and Design IV, FOSAD 2006/2007, Springer, LNCS 4677, pp. 160-182, 2007. DOI
Abstract
Critical Infrastructures are complex and highly interconnected systems that are crucial for the well-being of the society. Any type of failure can cause significant damage, affecting one or more sectors due to their inherent interdependency. Not only the infrastructures are critical, but also the information infrastructures that manage, control and supervise them. Due to the seriousness of the consequences, the protection of these critical (information) infrastructures must have the highest priority. It is the purpose of this book chapter to review and discuss about these infrastructures, to explain their elements, and to highlight their research and development issues. This chapter will also discuss the role of Wireless Sensor Network (WSN) technology in the protection of these infrastructures.

European CIIP Newsletter, vol. 11, issue 26, no. 1, European CIIP Newsletter, pp. 27-29, 03/2017.

IEEE Security & Privacy , vol. 20, issue 1, IEEE, pp. 23 - 32, 01/2022. DOI
Abstract
This article introduces a privacy manager for IoT data based on Edge Computing. This poses the advantage that privacy is enforced before data leaves the control of the user, who is provided with a tool to express data sharing preferences based on a novel context-aware privacy language.

VII Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2022), pp. 122-129, 06/2022.
Abstract
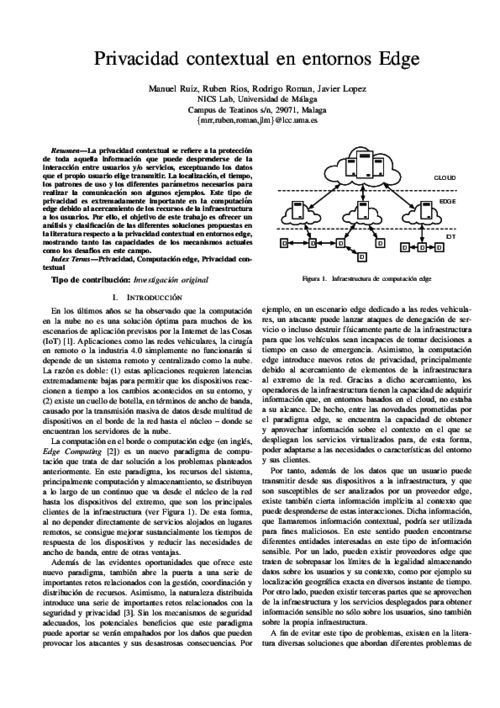
La privacidad contextual se refiere a la protección de toda aquella información que puede desprenderse de la interacción entre usuarios y/o servicios, exceptuando los datos que el propio usuario elige transmitir. La localización, el tiempo, los patrones de uso y los diferentes parámetros necesarios para realizar la comunicación son algunos ejemplos. Este tipo de privacidad es extremadamente importante en la computación edge debido al acercamiento de los recursos de la infraestructura a los usuarios. Por ello, el objetivo de este trabajo es ofrecer un análisis y clasificación de las diferentes soluciones propuestas en la literatura respecto a la privacidad contextual en entornos edge, mostrando tanto las capacidades de los mecanismos actuales como los desafíos en este campo.