CRITICAL INFRASTRUCTURES PROTECTION
Critical (Information) Infrastructure Protection (CIIP/CIP) is becoming one of the main fields of research in recent years. Private and public entities are joining forces to offer attractive solutions to face threat situations that may alter the operational continuity of a system and the efficient delivery of services to end users (citizens, industries, governments, etc.). However, this is not such a trivial task, mainly because these types of systems are increasingly dependent on Information Technologies (IT) for the management of critical services and automation of systems. What is more, this level of dependence indirectly demands that security and protection aspects of information systems and technologies must be taken into account, where prevention[1][2][3], advanced detection[4][5][6][7][8], response[9], recovery[10][11][12][13] and situational awareness[2][14] should be considered priority services[15], especially against Advanced and Persistent Threats (APTs)[16][17][18][19]. Advanced and stealthy attacks[20][21] may undoubtedly jeopardize the operational performance, safety and security of critical systems, causing spillover effects that may drastically spread to other critical infrastructures (even affecting their supply chain[22]).
Within this line of research, the NICS Lab team intends to address multiple defense strategies by considering the current industrial paradigms, such as Industry 4.0/5.0, and their related IT/Operational Technologies (OT). Among the technologies, we highlight digital twins, Artificial Intelligence (AI)/Machine Learning (ML), cloud/edge, blockchain, 6G, Industrial Internet of Things (IIoT) and Cyber-Physical Systems (CPS).
Industry 4.0/5.0
The advent of Industry 4.0/5.0[23][24], also known as the fourth/fifth industrial revolution, aims to drive IT networks with OT[25]. The idea is to create autonomous IT-OT environments with the ability to improve the value chain and production costs, but also human centricity, sustainability and resilience[26][22]. For that reason, Industry 4.0/5.0 paradigm constitutes a complex technological scenario (see Fig. 1) in which new and legacy devices have to coexist to share resources and data[12][27][28]. These devices may even connect to specific infrastructures or disruptive technologies, such as digital twins[24][29][30], blockchain[31][30], AI/ML[32][4][33][34], cloud/edge computing[35][27][36], IIoT[37] and 6G[24][30] for proper processing and storage of critical data. Moreover, this way of decentralizing resources allows the underlying infrastructures to efficiently manage operations, digitize processes and provide “smart” solutions in (near-)real time. But also this way of decentralizing systems and services leads to multiple types of security risks[38][39], especially in environments where control depends mainly on untrusted systems and communication protocols, such as ModbusTCP[20] and OCPP[40][33][41][42].
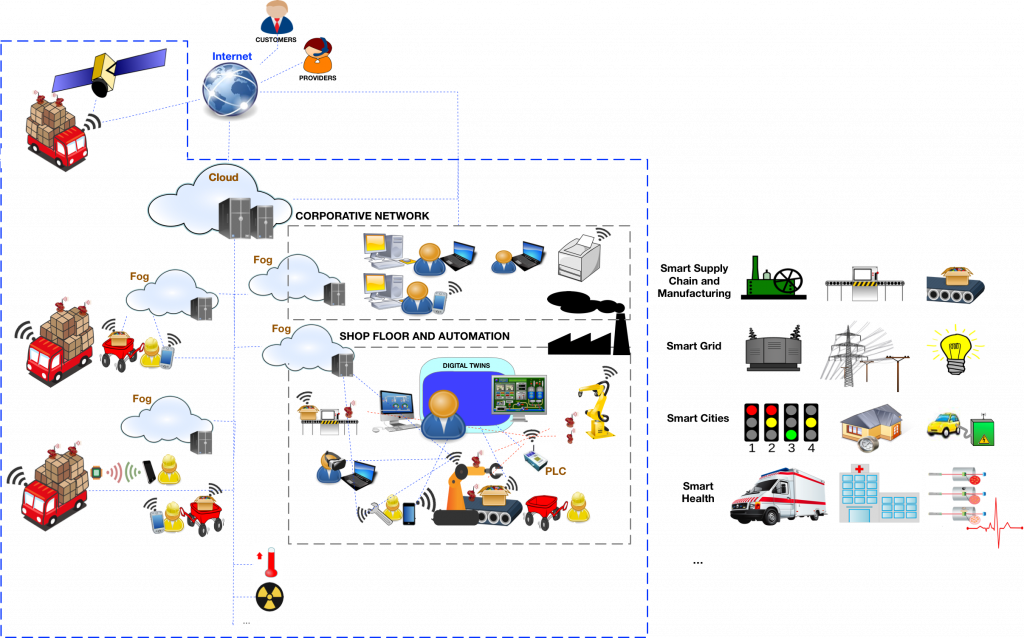
Within Industry 4.0/5.0, NICS Lab has extensive experience in the following application areas of:
- Manufacturing: SecTwin 5.0, SEGRES, Digital Aero, emapa 4.0, NERV, SADCIP, SADECEI-4.0, DISS-IIoT;
- Supply chain: CyberSec4Europe;
- Energy: CyberSecPro, DUCA, SealedGRID, CAIN, PERSIST, TIGRIS, SECRET, PROTECT-IC;
- Charging stations: Smart Secure II, Smart Secure I;
- Water: FACIES;
- Healthcare: CYBSEC-TECH;
- Communication: 5G+TACTILE;
- Mobility: DUCA, 5G+TACTILE;
In the manufacturing field, NICS Lab has been implied in several topics such as ethical hacking and penetration testing (emapa 4.0), cyber intelligence and OSSINT (NERV), and advanced resilience (SecTwin 5.0, SEGRES, Digital Aero, SADCIP, SADECEI-4.0, DISS-IIoT). In the supply chain of these manufacturing systems, NICS Lab has also been involved in the corresponding roadmap established as part of one of the four European pilot projects (CyberSec4Europe), and in the creation and maintenance of blockchain networks and nodes for this sector. Also, we have modelled multiple CPS/IIoT-based protection approaches for power systems (CyberSecPro, SECRET, PROTECT-IC) and energy subdomains such as Smart Grid (DUCA, SealedGRID, PERSIST, TIGRIS), microgrids and electric vehicle charging infrastructures (Smart Secure II, Smart Secure I). Considering these scenarios, we have addressed various studies on the efficient use and security level of current communication protocols such as Modbus/TCP[20], OCPP[41][42], ZigBee PRO[43], ISA100. 11a and WirelessHART[44], among others.
Throughout all these activities and research projects, we have not only learned about new vulnerabilities (e.g., through the deployment of honeypots) and cyber-attacks associated with energy control substations, but also vulnerabilities and threats associated with smart meters, which can corrupt the user’s privacy[45][46][47][48][49] – the last reference also explores other interconnection issues related to federated SealedGRID networks. In order to model complex CPSs for power neworks and show the control relationship between their elements, aspects associated with structural controllability and control theory (CAIN) have also been considered. We first studied the structural weaknesses of the control networks through the specification and implementation of multiple types of perturbations[50][51] to later explore recovery[52][13][12][10][53][54] and prediction solutions[53] for resilience.
As for water treatment control systems and in the FACIES context[55], NICS Lab has also been involved in prevention issues against stealth attacks[56] and in the study of methodologies for anomaly-based intrusion detection[56] and automatic response[9]. In order to reinforce the research, several analysis about the implications of ML models in prevention and detection techniques have also been provided[4][57][58]. In addition, this learning has served to expand concrete skills in the healthcare field (CYBSEC-TECH) in order to explore the level of goodness of industrial medical devices, and their susceptibility to types of attacks. In this process, specific topics of advanced detection with AI/ML and cyber intelligence have been extensively addressed, involving industry stakeholders and relevant technologies such as CPS, IoT/IIoT, edge and cloud.
Regarding dynamic detection of APTs, NICS Lab has not only applied advanced detection using AI/ML models, but also correlation mechanisms and consensus theories such as Opinion Dynamics[4][59][33][32]. Opinion Dynamics allows a system to detect anomaly states in widely complex and heterogenous networks, providing (local and global) health indicators, traceability mechanisms[17] and dependability (through QoS) in the industrial networks[60][18]. As a result of this study, several network traffic captures in Modbus/TCP can be downloaded from the IIoT-Testbed website of NISC Lab., which includes some traffic traces (considering normal and perturbed traffic) and graphics that show the effectiveness of the approach for IT-OT environments. As can be seen, the main expertise of the research team lies mainly in hunting for possible attacks[20][21][59][18][61][17] (the last reference includes practical results at IIoT-Testbed), wide-area situational awareness[62][56] and secure interconnection of critical systems[25][63][27][28][64][65][54][49][30][66], in addition to consider human intervention in these types of so critical facilities[67].


Digital Twins
- Manufacturing: Digital Aero, SecTwin 5.0, SEGRES, SADECEI-4.0;
- Aviation: Digital Aero;
- Mobility: DUCA, 5G+TACTILE;
- Communication: 5G+TACTILE;
The approach taken for the Digital Twin, and within these projects, is very varied. This has provided the research team with sufficient knowledge, experience and expertise in not only the deployment of Digital Twins for critical application scenarios, but the actual deployment of Digital Twins in critical infrastructures. Currently, we have several Digital Twins connected to an industrial model representing a manufacturing line (Training Factory Industry 4.0 type), with connection to real operational devices such as a robot and PLCs, and representing the digital world through 2D and 3D illustrations. All these Digital Twins have been designed so far for specific security and protection purposes. Among the proposals we highlight our experience in advanced detection through the use of Digital Twins and either for the prediction of attacks and lateral movements, the deployment of Digital Twins acting as honeypots for the analysis of risks and threats, the involvement of the Digital Twin for advanced response and recovery[11], as well as for access control[30]. In this analysis process the major difficulty encountered and even overcome has been the synchronisation of the physical and digital spaces. Synchronization is certainly a key process in maintaining the safety and security of the physical environment through Digital Twin, but also the security of Digital Twin is elemental if an appropriate level of security and resiliency is desired. Digital Twins contain all the intellectual property of the physical environment they simulate/emulate and represent. Thus, any threat posed to the Digital Twin, its underlying infrastructure (edge/cloud, virtualisation systems) and models (related to AI/ML, CAD, mathematical formulations, graphs, etc.) may entail a serious risk to the physical environment, including users, organisation(s) and value chain[29][24][22].
This experience gained has allowed the NICS Lab group to be part of multiple research proposals and international cooperation. For example, one of its members is currently Vice-Chair of the IEEE SIG ComSoc on Green Digital Twin Network, in addition to leading several invited talks and participating on specific technical program committees, special sections in high-impact journals such as IEEE Industrial Informatics, and WGs to address related topics. Indeed, NICS Lab has also been part of the coordination and edition of the ECSO Technical Paper (TP) on “Cybersecurity scenarios and Digital Twins” (May 2023), presenting the TP in several venues.
INDUSTRIAL CONTROL SYSTEMS
After the beginning of Industry 4.0/5.0, we have gradually witnessed how new developments have emerged in traditional control systems[68][69][70][71][72][73], and have allowed modernizing the current systems[74]. However, this technological evolution bring multiple security and safety risks[39] and vulnerabilities. Many of these vulnerabilities are caused by the strong IT-OT technological convergence, the connection to Internet infrastructures, and the lack of rigorous security policies and secure perimetral environment. Security systems (e.g., firewalls or intrusion detection systems) are normally based on inaccurate rules/patterns, interoperability issues and conflicts, abuse and use of weak security credentials based on username-password with high visibility and low update using insecure cryptosystems, vulnerable TCP/IP-based protocols, implementation bugs and insecure operating systems[75], non-segregation of functions, interferences or industrial noise, strong dependence on third-parties’ components, and so on[69][68][70][76][77].
The beginning of this line of research begins with the implications in PISCIS, CRISIS, ATENEA, PROTECT-IC and eCID, and in the development of the doctoral thesis “Interconnected Sensor Networks for Critical Information Infrastructure Protection” (C. Alcaraz). All this has allowed us to understand the main problems of SCADA (Supervisory Control and Data Acquisition) systems and control alternatives (e.g., wireless sensor networks (WSNs)[78][79][80][81][82][83][66] – see Fig. 2) for the 24/7 monitoring of control substations[84][69][72] without hampering with the minimal control requirements[76]. Today, many of the new alternatives not only aim at a local monitoring, but also to a remote monitoring. This means that it is necessary to study the TCP/IP connection benefits and drawbacks when traditional control devices (e.g., PLCs/RTUs) need to connect by themselves to centralized SCADA systems[84]. In this regards, it is vital to assess whether these elements as part of IoT/IIoT[84][85][86] are able to keep a suitable tradeoff between security and operational performance, and its viability for any critical scenario. In this sense, a risk management methodology has been specified in [39] to explore the role of IoT/IIoT and CPS technologies (also assessed in [87][74] but only for WSNs) in the diverse critical infrastructures (aircraft, SCADA systems, healthcare, etc.) and the cost that can cause a realistic cyber-attack (e.g., of the type of Stuxnet) in such technologies and environments.
References
- Cristina Alcaraz and Carmen Fernandez-Gago and Javier Lopez (2011): An Early Warning System based on Reputation for Energy Control Systems. In: IEEE Transactions on Smart Grid, vol. 2, no. 4, pp. 827-834, 2011, ISSN: 1949-3053.
- Cristina Alcaraz and Angel Balastegui and Javier Lopez (2010): Early Warning System for Cascading Effect Control in Energy Control Systems. In: 5th International conference on Critical Information Infrastructures Security (CRITIS’10), pp. 55-67, Springer Springer, Athens, Greece, 2010, ISSN: 0302-9743.
- Cristina Alcaraz and Isaac Agudo and Carmen Fernandez-Gago and Rodrigo Roman and Gerardo Fernandez and Javier Lopez (2009): Adaptive Dispatching of Incidences Based on Reputation for SCADA Systems. In: 6th International Conference on Trust, Privacy and Security in Digital Business (TrustBus’09), pp. 86-94, Springer-Verlag Springer-Verlag, Linz, Austria, 2009, ISBN: 978-3-642-03747-4.
- Jesus Cumplido and Cristina Alcaraz and Javier Lopez (2022): Collaborative anomaly detection system for charging stations. In: The 27th European Symposium on Research in Computer Security (ESORICS 2022), pp. 716–736, Springer, Cham Springer, Cham, 2022.
- Juan E. Rubio and Cristina Alcaraz and Rodrigo Roman and Javier Lopez (2019): Current Cyber-Defense Trends in Industrial Control Systems. In: Computers & Security Journal, vol. 87, 2019, ISSN: 0167-4048.
- Juan E. Rubio and Cristina Alcaraz and Rodrigo Roman and Javier Lopez (2017): Analysis of Intrusion Detection Systems in Industrial Ecosystems. In: 14th International Conference on Security and Cryptography (SECRYPT 2017), pp. 116-128, SciTePress SciTePress, 2017, ISBN: 978-989-758-259-2.
- Juan E. Rubio and Rodrigo Roman and Javier Lopez (2018): Analysis of cybersecurity threats in Industry 4.0: the case of intrusion detection. In: The 12th International Conference on Critical Information Infrastructures Security, pp. 119-130, Springer Springer, 2018.
- Lorena Cazorla and Cristina Alcaraz and Javier Lopez (2015): A Three-Stage Analysis of IDS for Critical Infrastructures. In: Computers & Security, vol. 55, no. November, pp. 235-250, 2015, ISSN: 0167-4048.
- Lorena Cazorla and Cristina Alcaraz and Javier Lopez (2015): Awareness and Reaction Strategies for Critical Infrastructure Protection. In: Computers and Electrical Engineering, vol. 47, pp. 299-317, 2015, ISSN: 0045-7906.
- Cristina Alcaraz and Stephen Wolthusen (2014): Recovery of Structural Controllability for Control Systems. In: Eighth IFIP WG 11.10 International Conference on Critical Infrastructure Protection, SRI International, Arlington, Virginia, USA, pp. 47-63, Springer Springer, Arlington, Virginia, USA, 2014, ISSN: 1868-4238.
- Andrew D. Syrmakesis and Cristina Alcaraz and Nikos D. Hatziargyriou (2022): Classifying resilience approaches for protecting smart grids against cyber threats. In: International Journal of Information Security, vol. 21, pp. 1189–1210, 2022, ISSN: 1615-5262.
- Cristina Alcaraz and Javier Lopez (2018): A Cyber-Physical Systems-Based Checkpoint Model for Structural Controllability. In: IEEE Systems Journal, vol. 12, pp. 3543-3554, 2018, ISSN: 1932-8184.
- Cristina Alcaraz (2017): Resilient Industrial Control Systems based on Multiple Redundancy. In: International Journal of Critical Infrastructures (IJCIS), vol. 13, no. 2/3, pp. 278 – 295, 2017, ISSN: 1741-8038.
- Cristina Alcaraz (2021): Situational Awareness for CPS. In: Encyclopedia of Cryptography, Security and Privacy, pp. 1–3, Springer Berlin Heidelberg, Berlin, Heidelberg, 2021, ISBN: 978-3-642-27739-9.
- Cristina Alcaraz and Meltem Sonmez (2013): PDR: A Prevention, Detection and Response Mechanism for Anomalies in Energy Control Systems. In: 7th International Conference on Critical Information Infrastructures Security (CRITIS 2012), pp. 22–33, Lillehammer, Norway, 2013.
- Juan E. Rubio and Cristina Alcaraz and Ruben Rios and Rodrigo Roman and Javier Lopez (2020): Distributed Detection of APTs: Consensus vs. Clustering. In: 25th European Symposium on Research in Computer Security (ESORICS 2020), pp. 174-192, 2020, ISBN: 978-3-030-58951-6.
- Juan E. Rubio and Rodrigo Roman and Cristina Alcaraz and Yan Zhang (2019): Tracking APTs in Industrial Ecosystems: A Proof of Concept. In: Journal of Computer Security, vol. 27, pp. 521-546, 2019, ISSN: 0167-4048.
- Juan E. Rubio and Rodrigo Roman and Cristina Alcaraz and Yan Zhang (2018): Tracking Advanced Persistent Threats in Critical Infrastructures through Opinion Dynamics. In: European Symposium on Research in Computer Security (ESORICS 2018), pp. 555-574, Springer Springer, Barcelona, Spain, 2018.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2020): Game Theory-Based Approach for Defense against APTs. In: 18th International Conference on Applied Cryptography and Network Security (ACNS’20), pp. 297-320, Springer Springer, 2020, ISBN: 978-3-030-57878-7.
- Cristina Alcaraz and Giuseppe Bernieri and Federica Pascucci and Javier Lopez and Roberto Setola (2019): Covert Channels-based Stealth Attacks in Industry 4.0. In: IEEE Systems Journal., vol. 13, pp. 3980-3988, 2019, ISSN: 1932-8184.
- Lorena Cazorla and Cristina Alcaraz and Javier Lopez (2018): Cyber Stealth Attacks in Critical Information Infrastructures. In: IEEE Systems Journal, vol. 12, pp. 1778-1792, 2018, ISSN: 1932-8184.
- Rodrigo Roman and Cristina Alcaraz and Javier Lopez and Kouichi Sakurai (2023): Current Perspectives on Securing Critical Infrastructures’ Supply Chains. In: IEEE Security & Privacy, vol. 21, no. 4, pp. 29-38, 2023, ISSN: 1540-7993.
- Javier Lopez and Cristina Alcaraz and Jesús Rodriguez and Rodrigo Roman and Juan E. Rubio (2017): Protecting Industry 4.0 against Advanced Persistent Threats. In: European CIIP Newsletter, vol. 11, no. 1, pp. 27-29, 2017.
- Cristina Alcaraz and Javier Lopez (2023): Protecting Digital Twin Networks for 6G-enabled Industry 5.0 Ecosystems. In: IEEE Network Magazine, vol. 37, no. 2, pp. 302-308, 2023, ISSN: 0890-8044.
- Cristina Alcaraz (2019): Secure Interconnection of IT-OT Networks in Industry 4.0. In: Critical Infrastructure Security and Resilience: Theories, Methods, Tools and Technologies, pp. 201-217, Springer International Publishing, 2019, ISBN: 978-3-030-00024-0.
- Simone Fischer-Hübner and Cristina Alcaraz and Afonso Ferreira and Carmen Fernandez-Gago and Javier Lopez and Evangelos Markatos and Lejla Islami and Mahdi Akil (2021): Stakeholder Perspectives and Requirements on Cybersecurity in Europe. In: Journal of Information Security and Applications, vol. 61, no. 102916, 2021, ISSN: 2214-2126.
- Cristina Alcaraz and Javier Lopez (2014): WASAM: A Dynamic Wide-Area Situational Awareness Model for Critical Domains in Smart Grids. In: Future Generation Computer Systems, vol. 30, pp. 146-154, 2014, ISSN: 0167-739X.
- Cristina Alcaraz and Javier Lopez (2014): Diagnosis Mechanism for Accurate Monitoring in Critical Infrastructure Protection. In: Computer Standards & Interfaces, vol. 36, pp. 501-512, 2014, ISSN: 0920-5489.
- Cristina Alcaraz and Javier Lopez (2022): Digital Twin: A Comprehensive Survey of Security Threats. In: IEEE Communications Surveys & Tutorials, vol. 24, no. thirdquarter 2022, pp. 1475 – 1503, 2022, ISSN: 1553-877X.
- Javier Lopez and Juan E. Rubio and Cristina Alcaraz (2021): Digital Twins for Intelligent Authorization in the B5G-enabled Smart Grid. In: IEEE Wireless Communications, vol. 28, pp. 48-55, 2021, ISSN: 1536-1284.
- Cristina Alcaraz and Juan E. Rubio and Javier Lopez (2020): Blockchain-Assisted Access for Federated Smart Grid Domains: Coupling and Features. In: Journal of Parallel and Distributed Computing, vol. 144, pp. 124-135, 2020, ISSN: 0743-7315.
- Alberto Garcia and Cristina Alcaraz and Javier Lopez (2023): MAS para la convergencia de opiniones y detección de anomalías en sistemas ciberfísicos distribuidos. In: VIII Jornadas Nacionales de Investigación en Ciberseguridad (JNIC), Vigo, Forthcoming.
- Cristina Alcaraz and Alberto Garcia and Javier Lopez (2022): Implicaciones de seguridad en MAS Desplegados en Infraestructuras de Carga basadas en OCPP. In: VII Jornadas Nacionales en Investigación en Ciberseguridad (JNIC 2022), pp. 172-179, 2022, ISBN: 978-84-88734-13-6.
- Francesco Flammini and Cristina Alcaraz and Emanuele Bellini and Stefano Marrone and Javier Lopez and Andrea Bondavalli (2022): Towards Trustworthy Autonomous Systems: Taxonomies and Future Perspectives. In: IEEE Transactions on Emerging Topics in Computing, 2022, ISSN: 2168-6750.
- Cristina Alcaraz (2018): Cloud-Assisted Dynamic Resilience for Cyber-Physical Control Systems. In: IEEE Wireless Communications, vol. 25, no. 1, pp. 76-82, 2018, ISSN: 1536-1284.
- Cristina Alcaraz and Isaac Agudo and David Nuñez and Javier Lopez (2011): Managing Incidents in Smart Grids à la Cloud. In: IEEE CloudCom 2011, pp. 527-531, IEEE Computer Society IEEE Computer Society, Athens, Greece, 2011, ISBN: 978-0-7695-4622-3.
- Cristina Alcaraz (2019): Security and Privacy Trends in the Industrial Internet of Things. Springer, 2019, ISBN: 978-3-030-12330-7.
- Ioannis Stellios and Panayiotis Kotzanikolaou and Mihalis Psarakis and Cristina Alcaraz (2021): Risk Assessment for IoT-Enabled Cyber-Physical Systems. In: Advances in Core Computer Science-Based Technologies, pp. 157-173, Springer International Publishing, Cham, 2021, ISBN: 978-3-030-41196-1.
- Ioannis Stellios and Panayiotis Kotzanikolaou and Mihalis Psarakis and Cristina Alcaraz and Javier Lopez (2018): Survey of IoT-enabled Cyberattacks: Assessing Attack Paths to Critical Infrastructures and Services. In: IEEE Communications Surveys and Tutorials, vol. 20, pp. 3453-3495, 2018, ISSN: 1553-877X.
- Cristina Alcaraz and Jesus Cumplido and Alicia Triviño (2023): OCPP in the spotlight: threats and countermeasures for electric vehicle charging infrastructures 4.0. In: International Journal of Information Security, 2023, ISSN: 1615-5262.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2018): Addressing Security in OCPP: Protection Against Man-in-the-Middle Attacks. In: 9th IFIP International Conference on New Technologies, Mobility & Security, 2018.
- Cristina Alcaraz and Javier Lopez and Stephen Wolthusen (2017): OCPP Protocol: Security Threats and Challenges. In: IEEE Transactions on Smart Grid, vol. 8, pp. 2452 – 2459, 2017, ISSN: 1949-3053.
- Remi Bars and Jorge Gomez and Mohamed Mahdi and Cristina Alcaraz and Rodrigo Roman (2011): Digital Home Networking: Standards. In: Carbou, Romain; Exposito, Ernesto; Roman, Rodrigo; Diaz, Michel (Ed.): Digital Home Networking, vol. 7130, pp. 60-96, John Wiley & Sons Inc., Reino Unido, 2011, ISSN: 978-1-84821-321-0.
- Cristina Alcaraz and Javier Lopez (2010): A Security Analysis for Wireless Sensor Mesh Networks in Highly Critical Systems. In: IEEE Transactions on Systems, Man, and Cybernetics, Part C: Applications and Reviews, vol. 40, no. 4, pp. 419-428, 2010, ISSN: 1094-6977.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2017): Selecting Privacy Solutions to Prioritise Control in Smart Metering Systems. In: The 11th International Conference on Critical Information Infrastructures Security, pp. 176-188, 2017.
- Sherali Zeadally and Al-Sakib Khan Pathan and Cristina Alcaraz and Mohamad Badra (2012): Towards Privacy Protection in Smart Grid. In: Wireless Personal Communications, vol. 73, pp. 23-50, 2012, ISSN: 0929-6212.
- Farhan Siddiqui and Sherali Zeadally and Cristina Alcaraz and Samara Galvao (2012): Smart Grid Privacy: Issues and Solutions. In: 21st International Conference on Computer Communications and Networks (ICCCN), pp. 1-5, IEEE Computer Society IEEE Computer Society, Munich, Germany, 2012, ISBN: 978-1-4673-1543-2.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2017): Recommender System for Privacy-Preserving Solutions in Smart Metering. In: Pervasive and Mobile Computing, vol. 41, pp. 205-218, 2017, ISSN: 1574-1192.
- Aristeidis Farao and Juan E. Rubio and Cristina Alcaraz and Christoforos Ntantogian and Christos Xenakis and Javier Lopez (2019): SealedGRID: A Secure Interconnection of Technologies for Smart Grid Applications. In: 14th International Conference on Critical Information Infrastructures Security (CRITIS 2019), pp. 169-175, Springer, Cham Springer, Cham, 2019, ISBN: 978-3-030-37669-7.
- Cristina Alcaraz and Estefania Etcheves Miciolino and Stephen Wolthusen (2013): Structural Controllability of Networks for Non-Interactive Adversarial Vertex Removal. In: 8th International Conference on Critical Information Infrastructures Security, pp. 120-132, Springer Springer, Amsterdam, The Netherlands, 2013, ISSN: 0302-9743.
- Cristina Alcaraz and Estefania Etcheves Miciolino and Stephen Wolthusen (2015): Multi-Round Attacks on Structural Controllability Properties for Non-Complete Random Graphs. In: The 16th Information Security Conference (ISC), pp. 140–151, Springer Springer, Springer International Publishing Switzerland, 2015.
- Cristina Alcaraz and Javier Lopez (2016): Safeguarding Structural Controllability in Cyber-Physical Control Systems. In: The 21st European Symposium on Research in Computer Security (ESORICS 2016), pp. 471-489, Springer Springer, Crete, Greece, 2016, ISBN: 978-3-319-45741-3.
- Javier Lopez and Juan E. Rubio and Cristina Alcaraz (2018): A Resilient Architecture for the Smart Grid. In: IEEE Transactions on Industrial Informatics, vol. 14, pp. 3745-3753, 2018, ISSN: 1551-3203.
- Cristina Alcaraz and Javier Lopez and Kim-Kwang Raymond Choo (2016): Dynamic Restoration in Interconnected RBAC-based Cyber-Physical Control Systems. In: Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (SECRYPT 2016), pp. 19-27, Lisboa, 2016, ISBN: 978-989-758-196-0.
- Cristina Alcaraz and Javier Lopez (2013): FACIES: online identification of Failure and Attack on interdependent Critical InfrastructurES. In: European CIIP Newsletter, vol. 7, pp. 11-13, 2013.
- Cristina Alcaraz and Javier Lopez (2013): Wide-Area Situational Awareness for Critical Infrastructure Protection. In: IEEE Computer, vol. 46, no. 4, pp. 30-37, 2013, ISSN: 0018-9162.
- Cristina Alcaraz and Lorena Cazorla and Gerardo Fernandez (2015): Context-Awareness using Anomaly-based Detectors for Smart Grid Domains. In: 9th International Conference on Risks and Security of Internet and Systems, pp. 17-34, Springer International Publishing Springer International Publishing, Trento, 2015, ISBN: 978-3-319-17126-5.
- Lorena Cazorla and Cristina Alcaraz and Javier Lopez (2013): Towards Automatic Critical Infrastructure Protection through Machine Learning. In: 8th International Conference on Critical Information Infrastructures Security, pp. 197-203, Springer Springer, Amsterdam, The Netherlands, 2013, ISSN: 0302-9743.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2017): Preventing Advanced Persistent Threats in Complex Control Networks. In: European Symposium on Research in Computer Security, pp. 402-418, 22nd European Symposium on Research in Computer Security (ESORICS 2017) 22nd European Symposium on Research in Computer Security (ESORICS 2017), 2017.
- Juan E. Rubio and Mark Manulis and Cristina Alcaraz and Javier Lopez (2019): Enhancing Security and Dependability of Industrial Networks with Opinion Dynamics. In: European Symposium on Research in Computer Security (ESORICS2019), pp. 263-280, 2019.
- Cristina Alcaraz and Javier Lopez (2012): Addressing Situational Awareness in Critical Domains of a Smart Grid. In: 6th International Conference on Network and System Security (NSS 2012), pp. 58-71, Springer-Verlag Springer-Verlag, Wu Yi Shan, Fujian, China, 2012, ISSN: 978-3-642-34600-2.
- Cristina Alcaraz and Lorena Cazorla and Javier Lopez (2017): Cyber-Physical Systems for Wide-Area Situational Awareness. In: Cyber-Physical Systems: Foundations, Principles and Applications, pp. 305 – 317, Academic Press, Boston, 2017, ISBN: 978-0-12-803801-7.
- Cristina Alcaraz and Javier Lopez and Stephen Wolthusen (2016): Policy Enforcement System for Secure Interoperable Control in Distributed Smart Grid Systems. In: Journal of Network and Computer Applications, vol. 59, pp. 301–314, 2016, ISSN: 1084-8045.
- Cristina Alcaraz and Javier Lopez and Kim-Kwang Raymond Choo (2017): Resilient Interconnection in Cyber-Physical Control Systems. In: Computers & Security, vol. 71, pp. 2-14, 2017, ISSN: 0167-4048.
- Javier Lopez and Juan E. Rubio (2018): Access control for cyber-physical systems interconnected to the cloud. In: Computer Networks, vol. 134, pp. 46 – 54, 2018, ISSN: 1389-1286.
- Javier Lopez and Jose A. Montenegro and Rodrigo Roman (2006): Service-Oriented Security Architecture for CII based on Sensor Networks. In: 2nd International Workshop on Security Privacy and Trust in Pervasive and Ubiquitous Computing (SecPerU’06), pp. 1-6, IEEE Press IEEE Press, Lyon, France, 2006.
- Javier Lopez and Cristina Alcaraz and Rodrigo Roman (2013): Smart Control of Operational Threats in Control Substations. In: Computers & Security, vol. 38, pp. 14-27, 2013, ISSN: 0167-4048.
- Cristina Alcaraz and Gerardo Fernandez and Fernando Carvajal (2012): Security Aspects of SCADA and DCS Environments. In: Lopez, Javier; Wolthusen, Stephen; Setola, Roberto (Ed.): Critical Infrastructure Protection: Information Infrastructure Models, Analysis, and Defense, vol. 7130, pp. 120-149, Springer-Verlag, Heidelberger (Berlin, Alemania), 2012, ISSN: 0302-9743.
- Cristina Alcaraz and Javier Lopez and Jianying Zhou and Rodrigo Roman (2011): Secure SCADA Framework for the Protection of Energy Control Systems. In: Concurrency and Computation Practice & Experience, vol. 23, no. 12, pp. 1414-1430, 2011, ISSN: 1532-0626.
- Cristina Alcaraz and Gerardo Fernandez and Rodrigo Roman and Angel Balastegui and Javier Lopez (2008): Gestión segura de redes SCADA. In: Nuevas tendencias en gestión de redes, Novática, no. 196, pp. 20-25, 2008, ISSN: 0211-2124.
- Cristina Alcaraz and Sherali Zeadally (2015): Critical Infrastructure Protection: Requirements and Challenges for the 21st Century. In: International Journal of Critical Infrastructure Protection (IJCIP), vol. 8, pp. 53–66, 2015, ISSN: 1874-5482.
- Cristina Alcaraz and Gerardo Fernandez and Rodrigo Roman and Angel Balastegui and Javier Lopez (2008): Secure Management of SCADA Networks. In: Novatica, New Trends in Network Management, vol. 9, no. 6, pp. 22-28, 2008, ISSN: 1684-5285.
- Cristina Alcaraz and Rodrigo Roman and Pablo Najera and Javier Lopez (2010): Acceso seguro a redes de sensores en SCADA a través de Internet. In: XI Reunión Española sobre Criptología y Seguridad de la Información (RECSI 2010), pp. 337-342, Tarragona (Spain), 2010, ISBN: 978-84-693-3304-4.
- Javier Lopez and Cristina Alcaraz and Rodrigo Roman (2007): On the Protection and Technologies of Critical Information Infrastructures.. In: On Foundations of Security Analysis and Design IV, FOSAD 2006/2007, Springer, vol. 4677, pp. 160-182, 2007, ISSN: 0302-9743, (10.1007/978-3-540-74810-6_6).
- Luca Faramondi and Marta Grassi and Simone Guarino and Roberto Setola and Cristina Alcaraz (2022): Configuration vulnerability in SNORT for Windows operating systems. In: 2022 IEEE International Conference on Cyber Security and Resilience (IEEE CSR), pp. 82-89, IEEE IEEE, https://www.ieee-csr.org, 2022, ISBN: 978-1-6654-9952-1.
- Cristina Alcaraz and Javier Lopez (2012): Analysis of Requirements for Critical Control Systems. In: International Journal of Critical Infrastructure Protection (IJCIP), vol. 5, pp. 137–145, 2012, ISSN: 1874-5482.
- Cristina Alcaraz and Sherali Zeadally (2013): Critical Control System Protection in the 21st Century: Threats and Solutions. In: IEEE Computer, vol. 46, no. 10, pp. 74 – 83, 2013, ISSN: 0018-9162.
- Cristina Alcaraz and Javier Lopez and Rodrigo Roman and Hsiao-Hwa Chen (2012): Selecting key management schemes for WSN applications. In: Computers & Security, vol. 31, no. 38, pp. 956–966, 2012, ISSN: 0167-4048.
- Rodrigo Roman and Cristina Alcaraz and Javier Lopez and Nicolas Sklavos (2011): Key management systems for sensor networks in the context of the Internet of Things. In: Computers & Electrical Engineering, vol. 37, pp. 147-159, 2011, ISSN: 0045-7906.
- Rodrigo Roman and Javier Lopez and Cristina Alcaraz and Hsiao-Hwa Chen (2011): SenseKey – Simplifying the Selection of Key Management Schemes for Sensor Networks. In: 5th International Symposium on Security and Multimodality in Pervasive Environments (SMPE’11), IEEE IEEE, Singapore, 2011.
- Javier Lopez and Rodrigo Roman and Cristina Alcaraz (2009): Analysis of Security Threats, Requirements, Technologies and Standards in Wireless Sensor Networks. In: Foundations of Security Analysis and Design 2009, pp. 289-338, Springer Berlin/Heidelberg Springer Berlin/Heidelberg, Bertinoro (Italy), 2009, ISSN: 0302-9743 (Print) 1611-3349 (Online).
- Cristina Alcaraz and Rodrigo Roman and Javier Lopez (2008): Análisis de la Aplicabilidad de las Redes de Sensores para la Protección de Infraestructuras de Información Críticas. In: VI Jornadas de Ingeniería Telemática (JITEL’08), pp. 437, Alcalá de Henares (Spain), 2008, ISBN: 978-84-612-5474-3.
- Cristina Alcaraz and Rodrigo Roman (2006): Applying Key Infrastructures for Sensor Networks in CIP/CIIP Scenarios. In: 1st International Workshop on Critical Information Infrastructures Security (CRITIS’06), pp. 166-178, Springer Berlin / Heidelberg Springer Berlin / Heidelberg, 2006, ISSN: 0302-9743 (Print) 1611-3349 (Online).
- Cristina Alcaraz and Rodrigo Roman and Pablo Najera and Javier Lopez (2013): Security of Industrial Sensor Network-based Remote Substations in the context of the Internet of Things. In: Ad Hoc Networks, vol. 11, pp. 1091–1104, 2013, ISSN: 1570-8705.
- Cristina Alcaraz and Javier Lopez (2017): Secure Interoperability in Cyber-Physical Systems. In: Security Solutions and Applied Cryptography in Smart Grid Communications, IGI Global, USA, pp. 137-158, IGI Global, USA, 2017, ISBN: 9781522518297.
- Rodrigo Roman and Javier Lopez and Cristina Alcaraz (2009): Do Wireless Sensor Networks Need to be Completely Integrated into the Internet?. In: 3rd CompanionAble Workshop – Future Internet of People, Things and Services (IoPTS) eco-Systems, pp. xxxx, xxxx xxxx, Brussels (Belgium), 2009.
- Rodrigo Roman and Cristina Alcaraz and Javier Lopez (2007): The Role of Wireless Sensor Networks in the Area of Critical Information Infrastructure. In: Information Security Technical Report, vol. 12, no. 1, pp. 24-31, 2007, ISSN: 1363-4127.

