5G Security
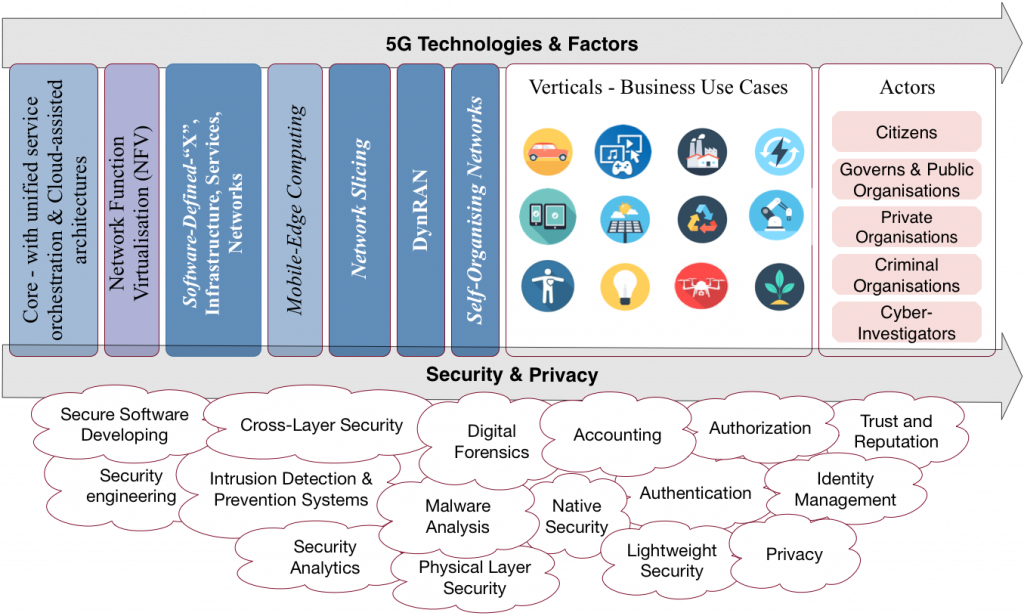
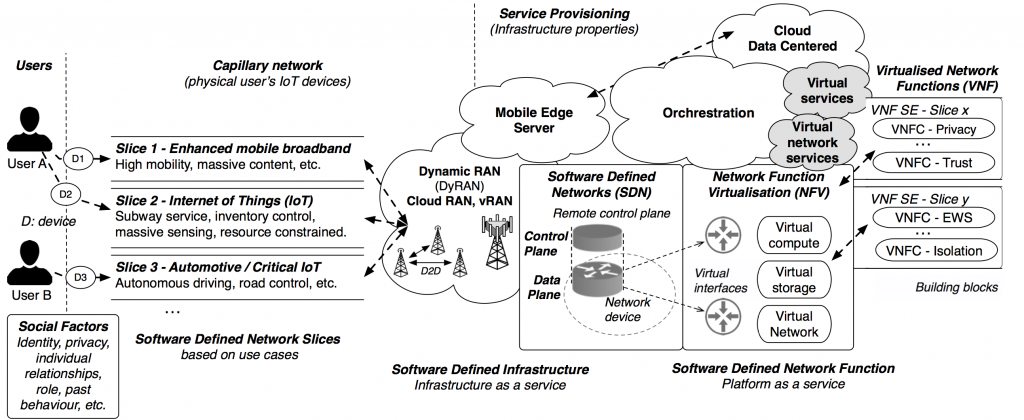
It sould be highlighted the impact of software-defined networks, infrastructures and services in the definition of 5G use cases. Indeed, the communication infrastructure is migrating to software-based architectures, more flexible than the previous ones, but also more complicated for orchestrating and managing distributed services. In this new technological ecosystem it will be fundamental to promote proactive security solutions that adapt to the context with great flexibility. Precisely, this is one of the main objectives pursued in the work we do in NICS lab. This goes far beyond providing real-time security solutions; it means that the 5G infrastructure will be prepared to be proactive by design. This requires defining the security requirements and deploying the basic enablers (e.g. specific software and hardware devices for security tasks) before deploying other security solutions. Thus, an important part of our research is to model different 5G scenarios in realistic simulations which make it possible for us to analyse the potential problems and offer solutions to them.
The following sections describe the main research lines in 5G carried out in NICS Lab.
Analysing cross-layer attacks
5G will rely on technologies that provide endlessnew technological opportunities; Networks do not longer rely onspecific hardware necessarily, as they can be software-defined, and a lot of their functions can be virtualized. This, whileintroducing greater flexibility, also exposes the network to greatersecurity risks. Therefore, the risk of a attack breaking intoa virtualized environment, or the presence of exploits in thesoftware used to define networks can bring down a wholeinfrastructure, and both can be targeted from devices whichare in acompletely different platform. Cross-layer attacks are particularly worrying, since they are difficult to categorise, identify and prevent. This, paired with the availability of devicesthat have more connectivity and new technologies that allow the expansion of attacks quite easily make it a very concerning scenario.
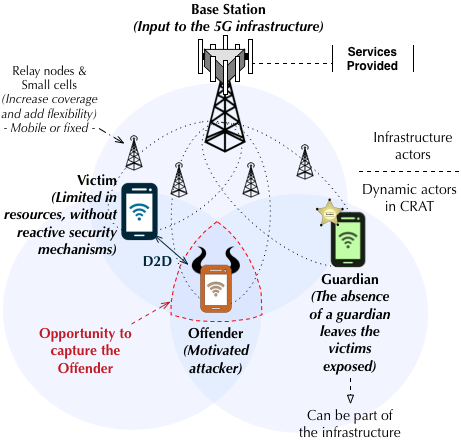
As a particular use case of this type of attacks, cross-platform attacks are analysed in [1], where the architecture BTV (bearer, transmitter and victim) is formalized for the analysis of this type of attacks. Cross-platform attacks are not new, but their effect on 5G networks can be much more devastating if intermediate architectures are not ready to recognize them. An important challenge lies in including inter-layer detectors capable of detecting attacks of this nature.
Proactive Digital Forensics in 5G-IoT
Proactive digital forensics is a relatively new term that has not yet been applied to 5G environments. Unlike traditional digital forensics, proactive approaches are more dynamic, enabling the system to collect digital evidence periodically, without stopping the functioning of the IT infrastructure (in optimal cases). Although not all systems support this type of action, proactive digital forensic solutions for 5G would allow them to slow down attacks if these are combined with known network security elements (e.g. IDS, SIEMs).
A formalisation of these issues in 5G environments is provided in [2]. The analysis extracts the requirements that should be considered considering four layers: end-user, application, control and infrastructure, following the natural architecture of a software-defined environment. In addition to showing the requirements per layer, it is sought to break down the inter-layer requirements to facilitate the identification of common requirements. In general, the analysis carried out is aimed at finding ways to facilitate orchestration and cooperation between services at different levels. Indeed, the need to seek cooperation mechanisms for 5G-IoT environments is argued in [3]. In this case, different forms of crowdsourcing applicable to the 5G-ToT ecosystem are analysed, and a proof of concept considering the Digital Witness solution is shown. Precisely, one of the priority actions in this line is the implementation of a prototype that demonstrates the possible acquisition and management of electronic evidence satisfying digital forensic requirements in 5G-IoT ecosystems, following the IoT-Forensic approach impulsed by the IoTest project. A first proof of concept of this approach has been successfully implemented using the open-source simulator OMNET++. The results, published in [4], show the advantages of employing devices that act as guardians of the communications infrastructure.
These guardians can be either, software or physical, but they must cooperate to improve detection and recovery from attacks. In particular, this work focuses on attacks based on proximity that mainly affect the last layers, closer to the user. However, they would be extensible to other levels.
Security and qos trade-offs in 5g
The growing number of parameters in heterogeneous networks, as is the case of the fifth generation (5G) Green networks, greatly complicates the analysis of the Security and Quality of Service Tradeoff (SQT). However, studying these types of relationships is crucial in Future Internet scenarios to prevent potential points of failure and to enhance the use of limited resources, increasing the user’s experience. Therefore, it is fundamental to provide tools and models for training, so that the users understand these dependencies and solve them prior to deploying new solutions.
In a 5G Green relay environment, the nodes can cooperate to send information to the destination, generating large amounts of data, from which information about the user’s preferences, network performance, and QoS can be inferred. This information can be useful to identify the effect that different technologies and configurations have on security and QoS.
These dependencies at different layers at a given moment can be understood as the context of a system. As 5G Green relay networks can involve from low-complexity personal devices to more powerful devices, assessing the security and QoS tradeoff is highly complex; it depends on the mechanisms to be deployed in a heterogeneous, dynamic and unpredictable environment. However, the final configuration of the environment cannot be independent from the analysis of the security and QoS tradeoff.
The Security and QoS Tradeoff Recommendation System (SQT-RS) presented in [5] is a first step in this direction. The specification can be used in 5G Green parametric-based systems to provide recommendations based on different goals, and contexts are generated dynamically, based on the user’s input. SQT-RS has been implemented to provide recommendations in Context-based Parametric Relationship Model (CPRM) compliant scenarios with large numbers of parameters [6], based on the requirements of various types of relays in 5G networks [7].
References
- Antonio Acien and Ana Nieto and Javier Lopez (2018): Modelo para la clasificación y análisis de ataques Cross-Platform. In: IV Jornadas Nacionales de Investigación en Ciberseguridad (JNIC 2018), Servicio Editorial de Mondragon Unibertsitatea Servicio Editorial de Mondragon Unibertsitatea, Donostia-San Sebastián (España), 2018, ISBN: 978-84-09-02697-5.
- Ana Nieto (2018): An Overview of Proactive Forensic Solutions and its Applicability to 5G. In: IEEE 5G World Forum (5GWF), pp. 191-196, IEEE, Santa Clara (USA), 2018, ISBN: 978-1-5386-4982-4.
- Ana Nieto and Antonio Acien and Gerardo Fernandez (2018): Crowdsourcing analysis in 5G IoT: Cybersecurity Threats and Mitigation. In: Mobile Networks and Applications (MONET), pp. 881-889, 2018, ISSN: 1383-469X.
- Ana Nieto and Antonio Acien and Javier Lopez (2018): Capture the RAT: Proximity-based Attacks in 5G using the Routine Activity Theory. In: The 16th IEEE International Conference on Dependable, Autonomic and Secure Computing (DASC 2018), pp. 520-527, IEEE IEEE, Athens, Greece, 2018, ISBN: 978-1-5386-7518-2.
- Ana Nieto and Nikolaos Nomikos and Javier Lopez and Charalambos Skianis (2017): Dynamic Knowledge-based Analysis in non-Secure 5G Green Environments using Contextual Data. In: IEEE Systems Journal, vol. 11, no. 99, pp. 2479-2489, 2017, ISSN: 1932-8184.
- Ana Nieto and Javier Lopez (2014): A Context-based Parametric Relationship Model (CPRM) to Measure the Security and QoS tradeoff in Configurable Environments. In: IEEE International Conference on Communications (ICC’14), pp. 755-760, IEEE Communications Society IEEE Communications Society, Sydney (Australia), 2014, ISBN: 978-1-4799-2003-7.
- Nikolaos Nomikos and Ana Nieto and Prodromos Makris and Dimitrios N. Skoutas and Demosthenes Vouyioukas and Panagiotis Rizomiliotis and Javier Lopez and Charalambos Skianis (2015): Relay Selection for Secure 5G Green Communications. In: Telecommunication Systems, vol. 59, pp. 169-187, 2015, ISSN: 1018-4864.